Industry leaders use risk assessments to gain an understanding of their cybersecurity systems. LeveL5Cyber’s Rapid Risk Assessment (RRA) is an accelerated, interview-based conversation that focuses on ten foundational areas of the NIST CSF 2.0 Framework with a concentration on OT risk reduction. We tailor our rapid OT and cybersecurity risk assessments to meet the goals and business needs of the company’s OT security program.

What We Offer
decades of hands-on experience
- OT-Focused Assessments (NIST 800-82, NISTIR 8183, IEC62443, 800-171)
- NIST CSF Assessments for strategy development or annual baselines
- Third-Party Risk Assessments
- DFARS Assessments including Program Management for POAM remediation and Solution Development
- CMMC Readiness Assessments
- Application / Infrastructure Risk Assessments
Why Choose a Rapid Risk Assessment?
When time, clarity, or focus is limited, a Rapid Risk Assessment offers a practical path forward. This streamlined approach is designed for organizations that need fast, standards-based insights into their current security posture—without the overhead of a full-scale engagement. It’s an ideal option when timing, focus, or flexibility is a priority, enabling you to quickly surface the most relevant security gaps while maintaining alignment with established frameworks.
Whether you’re unsure where to prioritize your efforts, want to assess specific risk areas, or need a rapid, actionable insight to support immediate decisions, the Rapid Risk Assessment provides targeted visibility you can act on. It delivers a flexible option that fits your timeline and allows you to make informed decisions quickly, validate existing controls, or uncover security gaps before they escalate. This format is streamlined but deliberate, helping you zero in on high-priority risks and take informed steps forward.
How Our Rapid Risk Assessment Process Works
We built our Rapid Risk Assessment process for clarity and efficiency without cutting corners. Our multi-pronged approach includes:
- Working with your team to identify key assets and understand your operational environment
- Analyzing relevant threats
- Assessing system vulnerabilities
- Evaluating potential impacts based on likelihood and severity
The result is a prioritized view of risk—grounded in recognized frameworks but tailored to your unique objectives.
The result is a prioritized view of risk—grounded in recognized frameworks but tailored to your unique objectives.
What To Expect From a Rapid Risk Assessment
Each Rapid Risk Assessment delivers targeted results you can immediately act on. You’ll get a clear report highlighting key risks, organized by severity and likelihood, along with practical recommendations for mitigation. The goal is to give your team a clear direction—without unnecessary complexity.
While findings vary by environment, we frequently uncover issues such as:
- Legacy system vulnerabilities
- Poor or missing network segmentation
- Inadequate access controls
- Outdated or unsupported security protocols
These types of gaps often go unnoticed until they cause problems. We help bring them into focus—early—so you can address them with confidence.
What is the ROI and Value of a Rapid Risk Assessment?
The Rapid Risk Assessment provides measurable value by enabling faster, more informed decisions. With clear visibility into your most pressing risks, your team can allocate resources effectively, address gaps proactively, and avoid costly disruptions. It’s a streamlined way to strengthen your security posture without slowing down operations.
By focusing on actionable insights rather than broad diagnostics, the assessment supports compliance efforts, reduces downtime, and helps you prioritize what matters most. For organizations that need clarity on where to act—without committing to a lengthy engagement—it delivers a strategic and operational return on investment.
Competitive Advantages with LeveL5Cyber
Our commitment is to empower organizations with the actionable insights necessary to navigate the complex landscape of OT cybersecurity threats. At LeveL5Cyber, we work with organizations that keep our nation running. Our rapid OT risk assessments can offer:
- Prioritized paths to risk reduction
- Clarity on important steps to build foundational controls
- Expert guidance on OT controls and cyber-hygiene
Our leaders and highly skilled professionals have decades of experience understanding factory operations.
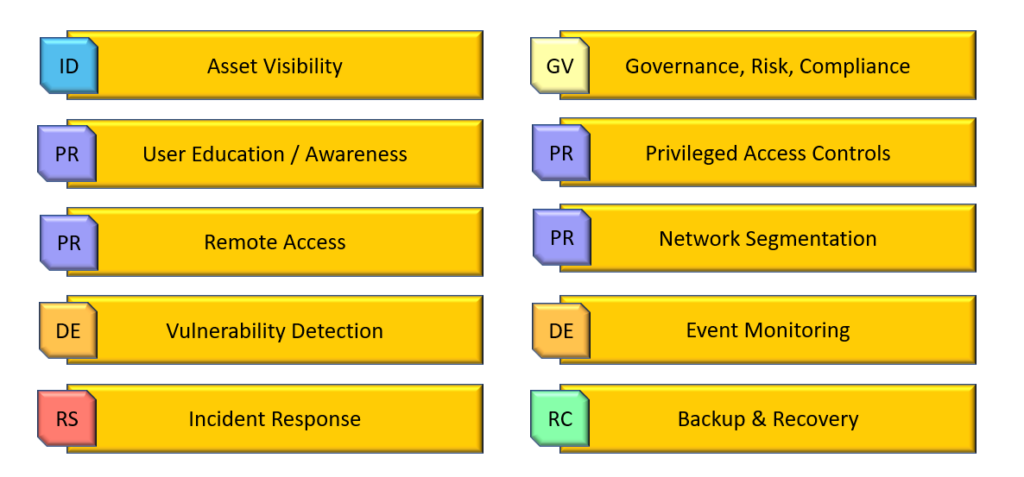
Notional 10 NIST CSF 2.0 OT categories
Rapid Risk Assessment (RRA) for Any Industry
Our tailored approach focuses on your industry-specific operations, allowing businesses to fortify against cyber-adversaries. Rapid OT and cybersecurity risk assessments are essential in industries such as Healthcare, Financial Services, and Defense that require a focus on foundational controls to build a mature cyber posture while reducing risk.
Other industries can benefit from this process:
Cybersecurity is an essential consideration at every step
Contact Us for Your Rapid Risk Assessment
When you’re looking to bolster your organization’s cybersecurity posture, a Rapid Risk Assessment (RRA) can help determine how to move forward safely, quickly and confidently. Contact LeveL5Cyber to get started.
Frequently Asked Questions
decades of hands-on experience
in cybersecurity
LeveL5Cyber’s Risk Assessments enable organizations to inform and prioritize decisions regarding cybersecurity. The services take into consideration today’s evolving threat landscape to drive cybersecurity priorities with an outcome-driven approach using industry standard processes.
While timing can vary, most Assessments will take approximately five to six weeks to complete. Program Development services may take longer based on the scope.
The ISA/IEC 62443 series of standards define requirements and processes for implementing and maintaining electronically secure industrial automation and control systems (IACS). These standards set best practices for security and provide a way to assess the level of security performance.
A NIST Special Publication provides guidance on how to secure operational technology (OT) while addressing their unique performance, reliability, and safety requirements. OT encompasses a broad range of programmable systems and devices that interact with the physical environment (or manage devices that interact with the physical environment). These systems and devices detect or cause a direct change through the monitoring and/or control of devices, processes, and events. Examples include industrial control systems, building automation systems, transportation systems, physical access control systems, physical environment monitoring systems, and physical environment measurement systems.
A NIST Special Publication that provides recommended requirements for protecting the confidentiality of controlled unclassified information (CUI)
Consult Our Experts
your security is important
*denotes a required field






